
SNOCC Quarterly Threat Update
Q1 2023

Written by: J.D. Butt, VP of Technology
Connect with J.D. on LinkedIn
Each quarter, the managed security team at Nexum shares insights from our first*defense® Security and Network Operations Command Centers (SNOCC). Nexum has been managing and monitoring the security environments of our customers since 2005. Therefore, we’re uniquely positioned to get an overall view of the threat landscape and observe attacks firsthand. Nexum will never publicly disclose specific, sensitive information; however, we can share observations and thoughts that might help your defense.
MACRO TRENDS
Exchange
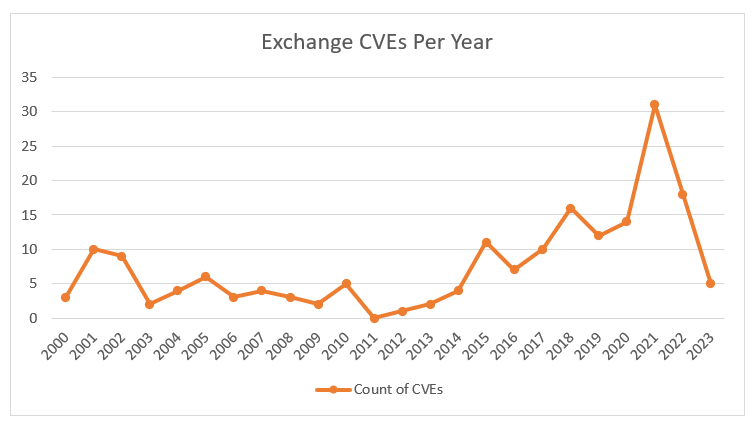 Vulnerabilities in Exchange continue to be a significant concern. Recently, once a vulnerability has been disclosed, we see several similar vulnerabilities around the same services over the next weeks and months; for example, ProxyShell (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207), ProxyLogon (CVE-2021-26855), and now ProxyNotShell (CVE-2022-41082). Like other vulnerabilities with each release, we see almost immediate scanning trying to identify and exploit boxes. Towards the very end of 2022, five common vulnerabilities and exposures (CVEs) were already assigned to the Exchange server! Given that an estimated 60,000 vulnerable servers are currently sitting on the internet, we highly recommend keeping exchange systems protected from direct internet access with solutions such as cloud-based email protection for Simple Mail Transfer Protocol (SMTP) or secure sockets layer (SSL) and virtual private network (VPN) technologies if OWA/ActiveSync is still in use by your organization.
Vulnerabilities in Exchange continue to be a significant concern. Recently, once a vulnerability has been disclosed, we see several similar vulnerabilities around the same services over the next weeks and months; for example, ProxyShell (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207), ProxyLogon (CVE-2021-26855), and now ProxyNotShell (CVE-2022-41082). Like other vulnerabilities with each release, we see almost immediate scanning trying to identify and exploit boxes. Towards the very end of 2022, five common vulnerabilities and exposures (CVEs) were already assigned to the Exchange server! Given that an estimated 60,000 vulnerable servers are currently sitting on the internet, we highly recommend keeping exchange systems protected from direct internet access with solutions such as cloud-based email protection for Simple Mail Transfer Protocol (SMTP) or secure sockets layer (SSL) and virtual private network (VPN) technologies if OWA/ActiveSync is still in use by your organization.
Socially Engineered Phishing
Another issue continues to be complex social engineering phishing attacks. We still see very targeted and well-crafted phishing attempts tailored to single organizations. These phishing attacks are increasingly made in parallel with the phone, SMS, or LinkedIn-based social engineering attacks. They often lead to issues with organizations that have not implemented multi-factor authentication. If push-based multi-factor authentication is the only method of protecting phished credentials, a breach can occur due to either fatigue or accidentally allowing a pushed authentication request. More advanced authentication is recommended to combine other conditions on authentication requests, such as location and device details.
IoT, Edge, and Infrastructure Devices
Vulnerable, exposed hosts and edge devices such as Firewall/VPN Appliances, IoT Devices, DVR Systems, Routers, and applications will be found and exploited if not patched. We continue to see heavy scanning by good and bad actors for unpatched devices. In the last 12 months, an abnormally large amount of infrastructure devices like firewalls have external-facing exploitable vulnerabilities. Opportunistic scanning for things that may be pulled out of a box and exposed to the internet continues to be high. We recommend putting a process in place to ensure that machines are properly patched, hardened, and protected with proper security controls before they are exposed to the internet.
Utilization of Geo-blocking and IP Blocklists
We still see many threats from countries such as Russia and China. We have had great success over the last few years by aligning where our customers do business with what is allowed on their firewalls. While this does not work for every organization or application, geography-based firewall blocking can block traffic from exposed hosts. To further protect resources, we highly recommend utilizing IP Block lists with firewalls to block inbound traffic from known malicious IP addresses. There are many lists to choose from, such as the Cisco Talos Blocklist or the Palo Alto Networks High-Risk IP Addresses List. As a managed security service provider (MSSP), Nexum offers its managed detection response (MDR) customers access to its catalog of curated threat data free as part of our subscriptions.
Contact Nexum
As always, the team at Nexum is here and ready to discuss these threats with you in more detail. Use our Talk to an Expert form to contact us.
Check Out More Resources

Juniper EX4000
Nexum’s, Allyn Crowe, breaks down what sets the latest EX4000 series switch apart—powerful PoE, multigig support for next-gen Wi-Fi, and faster performance. With quick boot times and seamless upgrades, it’s a smart choice for future-proofing networks.

Juniper Announces Wi-Fi 7 Access Points
Nexum’s engineering team highlights Juniper’s new Wi-Fi 7 AP47 as a game-changer, offering faster speeds, quad radios, and enhanced IoT capabilities. With dual 10Gbps interfaces and AI-driven Wi-Fi 7 support, these access points are designed for cutting-edge network performance.

AI-Native Now
Join Juniper Networks on June 5th for a LinkedIn Live exclusive discussion on “Leveraging AIOps for Maximum Impact.”

